In recent years, cloud software adoption rates have been skyrocketing. Despite the multitude of benefits that come with cloud computing, it's important for organisations to be able to recognise the risks of storing their data in the cloud; and what can be done for businesses to improve their data security in the cloud.
The statistics
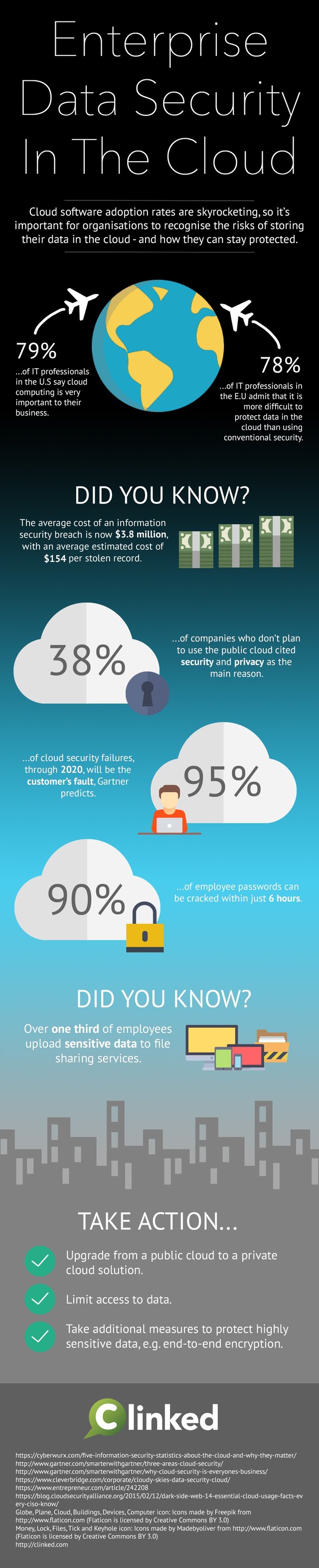
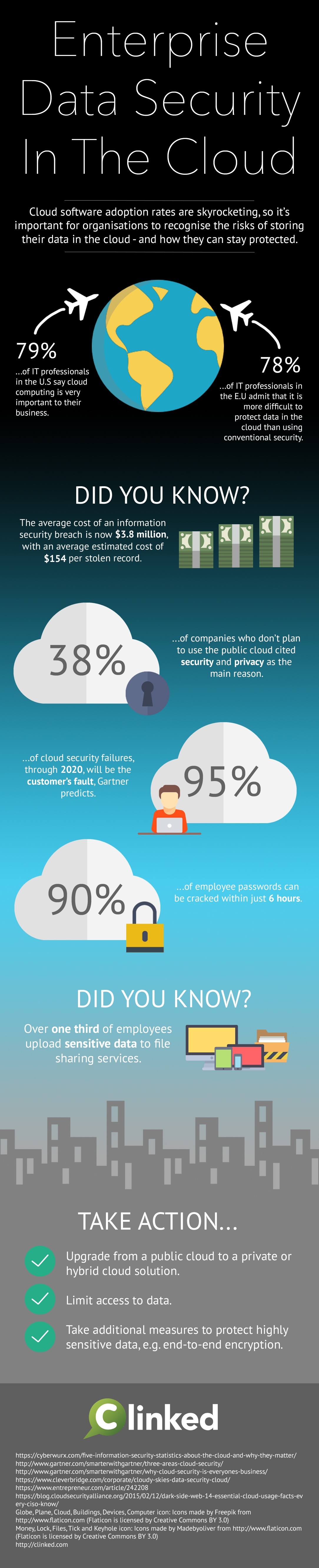
- 79% of IT professionals in the U.S. say cloud computing is very important to their business.
- 78% of IT professionals in the E.U. admit that it is more difficult to protect data in the cloud than using conventional security.
- 38% of companies who don't plan to use the public cloud cited security and privacy as the main reason.
- 95% of cloud security failures, through 2020, will be the customer's fault, Gartner predicts.
- 90% of employee passwords can be cracked within just 6 hours.
- The average cost of an information security breach is now $3.8 million, with an average estimated cost of $154 per stolen record.
- Over one third of employees upload sensitive data to file sharing services.
Take Action...
- Upgrade from a public cloud to a private cloud solution
In comparison to a public cloud, choosing a private cloud solution can improve your data security in the cloud; a private cloud will add an extra level of security to your software and improve performance.
Choose to implement a private cloud solution will be the equivalent of adopting on-premises software, except with a private cloud you will have more flexiblility and less costly options in terms of software scalability. What's more, private clouds provide businesses with greater control as they can be managed internally; this is ideal for organisations that have strict security and data regulations. Or, if you prefer, the software vendor can manage your private cloud solution.
(Don't know if you should implement Cloud Software or On-Premises? We wrote a post about the different delivery models here.)
- Limit access to data
By only limiting access to your data to those who actually need to use it, you will minimise the risk of your data:
A. Falling into the wrong hands,
B. Being compromised by employees/customers/hackers.
For example, you can increase your data security in the cloud by limiting access. You can do so by controlling your user permissions. Clinked offers such a feature: it allows the administrator to monitor who is accessing certain files and folders. This allows for greater control over managing sensitive data from within the software, thus reducing the risk of the information falling into the wrong hands or being compromised. Looking back at the infographic, it says that 95% of cloud security failures, through 2020, will be the customer's fault.
Carelessness, or 'human error', can often be the case with comprised data. For example employees who have access to sensitive data, that also have weak passwords (90% of employee passwords can be cracked within 6 hours), can fall victim to numerous cyber attacks. As can the employees and customers that try to access sensitive documents from coffee shops, using public Wi-Fi.
Would you leave your office at the end of the day, with the door unlocked? It's unlikely.
Of course, educating employees of the risks would be a start.
- Take additional measures to protect highly sensitive data, e.g. end-to-end encryption, multi factor authentication.
End-to-end encryption is a security mechanism that protects (encrypts) data as it is transferred from one end system (or device) to another. The idea behind end-to-end encryption is that no third-party will be able to gain access to your sensitive information as it is transported and stored.
Multi factor authentication is a method of computer access control; in order to gain access you will need to provide multiple, separate pieces of evidence to authenticate your identity. Forms of multi factor authentication can include knowledge (something you know); possession (something you have) and inherence (something you are).
Taking additional measures (like the two examples above) to protect your data will be extremely beneficial and should be implemented without a second thought. You will reduce the threat of cyber hackers and have peace of mind that your sensitive data is protected with the highest levels of security.
(Clinked offers both end-to-end encryption and multi factor authentication. Have a look here.)
Have a look around our website and sign up for your 10 day free trial if you think Clinked could be the right client portal for your business!







Let Us Know What You Thought about this Post.
Put your Comment Below.